- Home
- >
- DevOps News
- >
- 10 Steps to Simplify Your DevSecOps – InApps Technology
As the software industry continues to embrace the principles of DevOps, there is a growing push to adopt DevSecOps and prioritize security in the software development process from the very beginning. While the transition from DevOps to DevSecOps can be challenging, there are best practices that companies can follow to ensure a smooth transition and effectively integrate security into their workflow.
In this blog post, we will explore the 10 steps for a business to simplify its DevSecOps.
Key Summary
- Overview: The article by InApps Technology outlines ten practical steps to streamline DevSecOps, integrating security into DevOps workflows to enhance efficiency, reduce complexity, and ensure secure software delivery, with insights into tools, practices, and offshore solutions like those provided by InApps in Vietnam.
- What is DevSecOps?:
- Definition: DevSecOps embeds security practices within DevOps processes, ensuring continuous integration, delivery, and security throughout the software development lifecycle (SDLC).
- Purpose: Balances speed, quality, and security, minimizing vulnerabilities while maintaining rapid deployment cycles.
- Key Principles: Automation, collaboration, continuous monitoring, and shared responsibility for security.
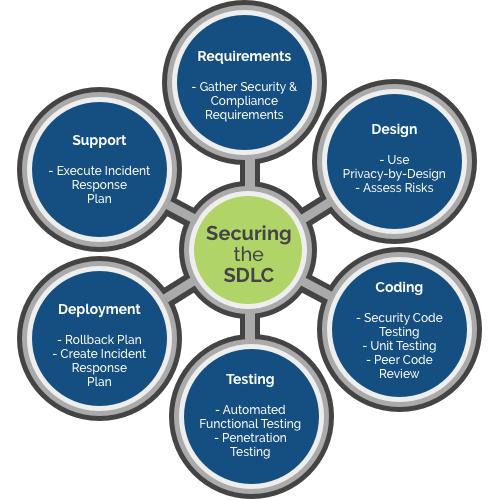
- 10 Steps to Simplify DevSecOps:
- 1. Foster a Security-First Culture:
- Step: Educate all teams (developers, operations, QA) on security’s importance, making it a shared responsibility.
- Action: Conduct regular training on secure coding, threat modeling, and compliance (e.g., OWASP Top 10).
- Impact: Reduces vulnerabilities by aligning teams on security goals.
- Example: Developers learn to sanitize inputs to prevent XSS attacks.
- 2. Integrate Security Early in the SDLC:
- Step: Embed security checks during planning and design, not just at testing or deployment.
- Action: Use threat modeling tools (e.g., Microsoft Threat Modeling Tool) and secure design principles.
- Impact: Catches issues early, reducing costly fixes later.
- Example: Identifying API vulnerabilities during the design of a fintech app.
- 3. Automate Security Testing:
- Step: Implement automated tools for static (SAST), dynamic (DAST), and dependency scanning.
- Action: Use tools like SonarQube (SAST), OWASP ZAP (DAST), and Snyk for dependency checks in CI/CD pipelines.
- Impact: Speeds up testing and ensures consistent vulnerability detection.
- Example: Automating Snyk scans to flag outdated libraries in a web app.
- 4. Use Infrastructure as Code (IaC):
- Step: Define infrastructure using code to ensure consistency and security.
- Action: Use Terraform or AWS CloudFormation with security templates; scan IaC for misconfigurations with Checkov.
- Impact: Reduces manual errors and enforces secure configurations.
- Example: Deploying a secure AWS VPC with Terraform scripts.
- 5. Implement Continuous Monitoring:
- Step: Monitor applications and infrastructure in real-time to detect and respond to threats.
- Action: Use tools like Prometheus, Grafana, or Splunk for logging and anomaly detection.
- Impact: Enables rapid incident response and compliance auditing.
- Example: Detecting unauthorized API access in a production environment.
- 6. Adopt Secure CI/CD Pipelines:
- Step: Integrate security checks into CI/CD workflows to maintain speed without compromising safety.
- Action: Use Jenkins, GitLab CI, or GitHub Actions with security gates (e.g., code scans, compliance checks).
- Impact: Ensures only secure code reaches production.
- Example: Blocking a deployment if a critical vulnerability is found in a GitLab pipeline.
- 7. Simplify Toolchains:
- Step: Consolidate tools to reduce complexity and improve team efficiency.
- Action: Choose integrated platforms (e.g., GitLab for CI/CD, SAST, and monitoring) over disparate tools.
- Impact: Minimizes learning curves and maintenance overhead.
- Example: Using GitLab’s built-in security scanning instead of multiple standalone tools.
- 8. Ensure Compliance and Governance:
- Step: Align DevSecOps with regulatory requirements (e.g., GDPR, HIPAA, SOC 2).
- Action: Automate compliance checks with tools like OpenSCAP and document processes for audits.
- Impact: Avoids legal penalties and builds customer trust.
- Example: Ensuring a healthcare app complies with HIPAA via automated data encryption checks.
- 9. Encourage Collaboration Across Teams:
- Step: Break silos between development, security, and operations for seamless workflows.
- Action: Use shared tools (e.g., Slack, Jira) and conduct cross-functional stand-ups or workshops.
- Impact: Accelerates issue resolution and aligns goals.
- Example: Dev and Sec teams collaborate on fixing a vulnerability during a sprint.
- 10. Leverage Offshore Expertise:
- Step: Augment teams with cost-effective, skilled developers from regions like Vietnam.
- Action: Partner with providers like InApps for DevSecOps implementation at $20–$50/hour vs. $80–$150/hour in U.S./EU.
- Impact: Saves 20–40% on costs while accessing expertise in secure development.
- Example: InApps delivers a secure CI/CD pipeline for a U.S. SaaS client.
- 1. Foster a Security-First Culture:
- Benefits of Simplified DevSecOps:
- Security: Reduces vulnerabilities through early and automated checks.
- Speed: Maintains rapid delivery with secure CI/CD pipelines.
- Cost Efficiency: Offshore expertise and automation lower development costs.
- Compliance: Ensures adherence to regulations, avoiding fines.
- Collaboration: Enhances team alignment, improving productivity.
- Challenges:
- Cultural Resistance: Teams may resist adopting security responsibilities.
- Tool Overload: Managing multiple tools can complicate workflows.
- Skill Gaps: Lack of DevSecOps expertise requires training or outsourcing.
- Balancing Speed and Security: Tight deadlines may tempt skipping security checks.
- Security Considerations:
- Encryption: Use TLS for data in transit and AES for data at rest.
- Access Control: Implement RBAC in CI/CD tools and infrastructure.
- Auditing: Log all pipeline activities for compliance (e.g., SOC 2).
- Vulnerability Management: Regularly update tools and dependencies to patch CVEs.
- Example: InApps secures a client’s pipeline with JWT authentication and Splunk logging.
- Use Cases:
- Fintech: Securing payment apps with automated SAST and compliance checks.
- Healthcare: Building HIPAA-compliant platforms with continuous monitoring.
- E-commerce: Deploying scalable, secure apps with IaC and CI/CD.
- Startups: Rapidly launching MVPs with offshore DevSecOps expertise.
- SaaS: Ensuring SOC 2 compliance for cloud-based services.
- InApps Technology’s Role:
- Leading HCMC-based provider with 500+ experts in DevSecOps, skilled in tools like Jenkins, Terraform, and Snyk.
- Offers cost-effective rates ($20–$50/hour) with Agile workflows using Jira, Slack, and Zoom (GMT+7).
- Provides end-to-end DevSecOps solutions, from secure pipeline setup to monitoring and compliance.
- Example: InApps implements a secure GitLab CI/CD pipeline for a U.S. fintech client, reducing vulnerabilities by 30%.
- Recommendations:
- Start with a security-first culture and early SDLC integration to simplify DevSecOps.
- Automate testing and monitoring to balance speed and security.
- Consolidate tools to streamline workflows and reduce complexity.
- Partner with InApps Technology for cost-effective, expert DevSecOps solutions, leveraging Vietnam’s talent pool for secure, efficient software delivery.
1. Promote a DevSecOps Culture
There are several definitions of DevSecOps, but the one that stands out universally is collaboration, automation, learning, measurements and sharing (CALMS), coined by Jez Humble and adopted further by Synopsys’s Meera Rao.
At its core, DevSecOps thrives on a culture and a mindset in which various cross-functional teams share a single goal of continuous software security.
To embed a culture of DevSecOps, it’s best to start with a few self-motivated and committed teams.
Your strategic initiatives act as guide rails for these teams while they work to ingrain DevSecOps culture into day-to-day functions, balancing security, speed and scale. From there, other teams can follow in their footsteps.
The key to promoting a DevSecOps culture and mindset is to operate in iterations. To learn more, read The best practices to adopt a DevOps culture.
2. Empower Teams to Build Security into the SDLC
While it sounds perfectly logical to “build security in,” it’s easier said than done. One of the key challenges that teams face is a lack of understanding, tooling, and processes that help build security into their software.
Ensuring that software is secure starts even before you write code. Security activities such as threat modeling and architecture reviews can help set the course for the security requirements and controls to be implemented during the software development life cycle (SDLC).
When implementing the requirements and controls, giving development teams enough training on how to write secure code and fix security issues is of utmost importance.
Ensuring visibility into security vulnerabilities also helps create awareness. For example, one way to give immediate feedback on the code is to use IDE-based scanners to identify insecure code right in the developer’s workstation. Such tooling enables developers to code securely and fix vulnerabilities early.
3. Plan Security Activities
Every organization that wants to integrate security into its DevOps workflows is likely to be torn between decisions about which security activities are needed and which type of tooling to buy.
The key is to think first about when a security activity is performed in an SDLC. Each organization works in its own unique way when adopting DevSecOps, driven by its industry, maturity, and culture. The placement of security checkpoints will be unique as well.
For example, when developers have adequate training in coding securely, they often find it useful to perform security testing before code commits happen.
That prevents developers from checking in unsecured code. For other organizations, the earliest starting point for security scanning could be in their central integration pipelines, which are normally triggered right after source code gets merged from developer branches to the main branch.
After determining when to perform security activities, each checkpoint can be used to indicate which security activity and tool is most applicable. In the example above, a pre-commit security scan or an IDE-based scan could be implemented to shift security testing further left in the development stage.
Additionally, the central integration pipelines could have more security checkpoints implemented, with activities such as deeper static application security testing (SAST), software composition analysis (SCA), dynamic application security testing (DAST)/interactive application security testing (IAST), or penetration testing.
4. Improve Speed and Scale with Automation
Automation is key when balancing security integrations with speed and scale. DevOps adoption already focuses on automation, and the same holds true for DevSecOp. Automating security tools and processes ensures teams are following DevSecOps best practices.
Automation ensures that tools and processes are used in a consistent, repeatable, and reliable manner. It’s important to identify which security activities and processes can be completely automated and which require some manual intervention.
For example, running a SAST tool in a pipeline can be automated entirely; however, threat modeling and penetration testing require manual efforts. The same is true for processes.
A successful automation strategy also depends on the tools and technology used. One important automation consideration is whether a tool has enough interfaces to allow its integration with other subsystems.
For example, to enable developers to do IDE scans, look for a SAST tool that has support for common IDE software.
Similarly, to integrate a tool into a pipeline, review whether the tool offers APIs or webhooks, or CLI interfaces that can be used to trigger scans and request reports.
Another consideration is a tool’s ability to be used “as code,” including configuration-as-code or pipeline-as-code, which can determine the level of automation that can be achieved throughout the SDLC.
As an example, a containerized AST tool can be deployed and run easily in an automated environment, due to its infrastructure-as-code capability. Similarly, continuous integration (CI) systems, like Jenkins CI, allow defining global libraries to provide pipelines-as-code features, which enables global AST integrations across a large number of CI jobs.
5. Start Early with Small Changes
Often, when organizations or teams start integrating security activities and scanners in a DevSecOps pipeline, they tend to enable an overwhelming scope of rule sets and scan configurations.
This hampers DevSecOps adoption in two ways:
- First, development teams suddenly see many security findings in their queues, which makes it impossible for them to address them all over a short sprint, and that causes reluctance to fix security findings.
- Second, the subsequent loss of dev support and acceptance threatens the entire DevSecOps culture.
It is key, therefore, to start early with small changes. Security testing should begin as early in the SDLC as possible and should be done with a gradually increasing scope.
For example, instead of enabling full scans or scans with the entire rule set for a pre-commit security checkpoint, teams should consider keeping the rule set limited to its top five vulnerabilities and running deeper scans later.
6. Tie in the Out-of-Band Activities
While automation plays an important role in adopting DevSecOps, there are certain types of security activities that must be done out of the band and manually.
Usually, these activities are performed on a predefined schedule, perhaps quarterly. This can result in either overdoing or underdoing those activities.
Triggering out-of-band activities based on events in an automated pipeline helps balance the requirement. For example, results of SAST scans that are anomalous or cross a threshold could trigger a deeper manual source code review.
Similarly, if a critical vulnerability is detected in a third-party component, a penetration test could be scheduled to assess its exploitability.
7. Manage Security Vulnerabilities as Software Defects
Security vulnerabilities are commonly reported differently than quality and functional defects. Often, organizations maintain the two types of findings — security and quality — in two different locations. This reduces the visibility each team and role has when they look at the overall security posture of their project.
Maintaining security and quality findings in one place helps teams treat both types of issues in the same manner and with the same importance.
In reality, security findings, especially ones from automated scanning tools, can be a false positive. It becomes challenging, in such cases, to ask developers to review and fix those problems.
One solution is to tune the security tooling over time by analyzing historical findings and application information, and by applying filters and custom rule sets to report only critical issues.
8. Collect and Analyze Data at Every Stage
You can measure success and failure by collecting data about the various factors and attributes contributing to DevSecOps and retrieving useful metrics from them. A comprehensive metrics program is one that includes people, process, and technology components holistically.
For instance, metrics should shed light on failures stemming from a lack of well-defined processes as well as inefficient tool use.
To achieve this, measuring and collecting relevant data at every stage of the pipeline and security activities is of paramount importance. Automation should also be used where possible to continuously and consistently gather the data points required for metrics.

There are numerous factors that can be measured and used to build metrics, such as the number and type of security scans performed throughout SDLC, the number of reported critical security and quality issues, the pipeline execution time, and more.
This data helps teams create metrics to move toward an overall reduction in defect density, preproduction security defects, and mean time to deployment.
9. Learn from Your Failures
DevSecOps adoptions are always iterative. During continuous integration and measurement, failures are bound to happen from time to time.
Ideally, failure should be used to help teams learn and improve. Any DevSecOps pipeline that doesn’t report a failure or take an action on one is not truly embracing DevSecOps.
The “Three Ways” principle of DevOps is also directly applicable to DevSecOps:
- First Way: Never passing a known failure or a known critical security defect into downstream work, thereby ensuring the success of the end-to-end system.
- Second way: Shorten the feedback loops by reporting any failure, including security, as soon as it happens.
- Third way: Build a more secure development culture by learning from past failures, iterating and tackling new failures/defects just as outlined in the first and second ways.
10. Improve Velocity with Scalable Governance
Traditional governance models significantly impede delivery velocity and are incompatible with the fundamental goal of DevSecOps: to ensure fast, safe and secure delivery of software. As a result, along with security testing, governance activities should also be automated where possible.
Governance-as-code should be used to implement checks across the software delivery pipeline, and it should include required triggers for manual intervention to handle escalations, and exceptions and implement compensating controls.
As an example of governance, consider signoff gates that an organization typically has before their releases.
Collaborating, obtaining buy-in, and enabling development and operations teams is key to ensuring that the governance model is inclusive and fully adopted. Such enablement can be achieved using various feedback mechanisms, which include, but are not limited to:
- Pausing the pipeline builds
- Sending notifications
- Creating defects and tracking them centrally
- Breaking/stopping the pipeline build completely
Put These Practices into Action
Transforming your organization to DevSecOps is a huge undertaking with many known and unknown challenges. It’s important to keep in mind that DevSecOps is not an off-the-shelf tool or a golden pipeline.
It will take a roadmap to become a reality for any organization. Follow these best practices to lay the foundation.
About InApps
InApps is an outsourcing and development company located in Vietnam. At InApps, we currently provide services on DevOps, Offshore Software Development, MVP App Development, and Custom App Development.
We’ve become a trusted partner of more than 60+ businesses from the US, the UK, and Europe to Hongkong from different industries.
More than being a partner, we aim to become the business’s companion. Therefore we continue to update helpful articles for those who are in need.
If you’re interested in DevOps topic, you might find those articles helpful: An A – Z introduction about DevOps that companies should keep in mind
Let’s create the next big thing together!
Coming together is a beginning. Keeping together is progress. Working together is success.



















